Posted on Nov 5, 2014
Elections and voter fraud - what we can do about it?
12.5K
105
80
2
2
0
My analysis of elections, voter fraud, and how we, as a country, can nearly 100% eliminate it...
Tonight, on the way home from my current job as a network administrator, I was listening to late night talk (you know the one - the one that is always talking about UFOs and Bigfoot...) Anyway, tonight the topic was voter fraud. George Noory (the host) had a guest on who was discussing how voter fraud is always going to be a problem, no matter what country you live in, or what voting procedures you have...
I found myself in complete disagreement. Sure, under current standards, with the technology we are currently fielding, we don't have a way to stop voter fraud, especially when states refuse to require people to have IDs so you can vouch that they are the actual people casting a ballot. I'm not trying to get into a political debate on this though... what I'm trying to point out, is that there is a way to stop voter fraud dead... as in, almost IMPOSSIBLE to commit. That's right... nearly impossible.
Here's how it works: Anyone in IT, is (or should be) familiar with the Public and Private key infrastructure that we use to encrypt and decrypt messages, as well as generating a hash value. Think of a package, within a package, within a package, and so on, much like the Russian wooden dolls that are hollow, and each time you open one, there's another doll inside it.. similar concept.. I know, this is complicated, so if you don't care, fine, but I do, and I think this will work 99-100%!
What we need to do, as a country/state, whatever, is every person should be able to pick up a Driver's license or state ID (even if it is subsidized) that proves who they say they are - let's call it a Personal ID or PID. Embedded in the PID, should be a smart chip. On the chip, just like on our CAC and PIV cards, is the person's encrypted private key, their public key, and a hash key. For those of you who don't understand this, bear with me for a minute.
When a person goes to vote, whether through a polling station, the internet, whatever, they insert their PID into the slot just like we do with a DoD CAC or PIV. They then cast their vote. When their vote is cast, several things happen:
First, the persons vote is recorded, and then encrypted with the person's private key. The only way to change it, is using the private key. However, you can decrypt it and read what was cast with the public key - just bear that in mind for a moment. So here's our package [encrypted vote]<-using person's private key
Second: The encrypted vote, combined with some personal identification values and the person's public key, is then hashed (that is, a hash is generated using the person's hash key).
Now our package looks like this: ([encrypted vote] + [personal id values] + [person's public key]) x [personal hash key] = [personal hash value]
Third: the encrypted vote, the person's ID values, the person's public key, and the person's hash are ALL encrypted using the Government's (or voting authority - doesn't matter what you call it) Public Key (yes, this is important, the government/voting authority must have both a public and private key, and a hash key as well). What this does is makes the info that was encrypted, unreadable UNLESS you have the private key for the voting authority.
Our package now looks like this: {[encrypted vote] + [personal id values] + [Personal hash key] + [Personal hash value] + [person's public key]} = [encrypted package] <-- using voting authority's public key
Fourth: The data is then REHASHED using the government's Hash key. [encrypted package] x [Voting Auth Hash Key] = [VA Hash Value]
Fifth: The encrypted data, and the generated hash are then both sent to the voting authority. So now our package: ([Encrypted package]+[VA Hash Value]) sent to Voting Auth.
Sixth: The voting authority, using their hash key, re-hashes the encrypted package, the same as step four above. This should create the exact same hash key, which verifies that the encrypted data was NOT tampered with during transmission to the Voting Authority.
SO [encrypted package] x [Voting Auth Hash Key] should still = [VA Hash Value]
The package can now be stripped of the hash value that was sent with it:
[Encrypted Package]
7th: The Voting Authority takes private key that belongs to them, decrypts the data. Since the package was sent with the VA's public key, the only key that can decrypt it is the private key the VA has. This gets them to here:
[encrypted vote] + [personal id values] + [person's hash key] + [person's hash value] + [person's public key] <-- decrypted with VA's private key.
8th: The voting authority can take the person's hash key, and re-hash the encrypted votes with that person's ID values - if the encrypted vote data and the person's ID data was not tampered with, the hash key should generate the SAME hash value that was sent with all the other data to them.
So ([encrypted vote] + [personal id] + [person's public key]) x [personal hash] should still = [personal hash value]
9th: Since the hash value they generated above should be the same as what was transmitted, the VA can now decrypt the encrypted vote using the person's public key.
The entire process does the following: 1) It makes the vote unalterable. If it is altered, the hash values change and won't match. 2) it makes the vote irrefutable - the person can't say they didn't cast the ballot, because their personal ID is tied to the vote. 3) it makes the the vote nearly 100% unforge-able. Because the vote is tied to the person's personal data that only they will have, it can't be forged and if it is, the person can almost 100% prove they didn't send the vote. 4) no one on either end can tamper with the vote results, and if they do it becomes instantly obvious. 5) LAST, and most important, it makes it so that if there is EVER a question about the vote, an independent party can come in and verify all of the above.
So for those of you who understood every step I described above, what do you think? Leave me some feedback or vote below!
Thanks.
V/R
Marc Wayman
Tonight, on the way home from my current job as a network administrator, I was listening to late night talk (you know the one - the one that is always talking about UFOs and Bigfoot...) Anyway, tonight the topic was voter fraud. George Noory (the host) had a guest on who was discussing how voter fraud is always going to be a problem, no matter what country you live in, or what voting procedures you have...
I found myself in complete disagreement. Sure, under current standards, with the technology we are currently fielding, we don't have a way to stop voter fraud, especially when states refuse to require people to have IDs so you can vouch that they are the actual people casting a ballot. I'm not trying to get into a political debate on this though... what I'm trying to point out, is that there is a way to stop voter fraud dead... as in, almost IMPOSSIBLE to commit. That's right... nearly impossible.
Here's how it works: Anyone in IT, is (or should be) familiar with the Public and Private key infrastructure that we use to encrypt and decrypt messages, as well as generating a hash value. Think of a package, within a package, within a package, and so on, much like the Russian wooden dolls that are hollow, and each time you open one, there's another doll inside it.. similar concept.. I know, this is complicated, so if you don't care, fine, but I do, and I think this will work 99-100%!
What we need to do, as a country/state, whatever, is every person should be able to pick up a Driver's license or state ID (even if it is subsidized) that proves who they say they are - let's call it a Personal ID or PID. Embedded in the PID, should be a smart chip. On the chip, just like on our CAC and PIV cards, is the person's encrypted private key, their public key, and a hash key. For those of you who don't understand this, bear with me for a minute.
When a person goes to vote, whether through a polling station, the internet, whatever, they insert their PID into the slot just like we do with a DoD CAC or PIV. They then cast their vote. When their vote is cast, several things happen:
First, the persons vote is recorded, and then encrypted with the person's private key. The only way to change it, is using the private key. However, you can decrypt it and read what was cast with the public key - just bear that in mind for a moment. So here's our package [encrypted vote]<-using person's private key
Second: The encrypted vote, combined with some personal identification values and the person's public key, is then hashed (that is, a hash is generated using the person's hash key).
Now our package looks like this: ([encrypted vote] + [personal id values] + [person's public key]) x [personal hash key] = [personal hash value]
Third: the encrypted vote, the person's ID values, the person's public key, and the person's hash are ALL encrypted using the Government's (or voting authority - doesn't matter what you call it) Public Key (yes, this is important, the government/voting authority must have both a public and private key, and a hash key as well). What this does is makes the info that was encrypted, unreadable UNLESS you have the private key for the voting authority.
Our package now looks like this: {[encrypted vote] + [personal id values] + [Personal hash key] + [Personal hash value] + [person's public key]} = [encrypted package] <-- using voting authority's public key
Fourth: The data is then REHASHED using the government's Hash key. [encrypted package] x [Voting Auth Hash Key] = [VA Hash Value]
Fifth: The encrypted data, and the generated hash are then both sent to the voting authority. So now our package: ([Encrypted package]+[VA Hash Value]) sent to Voting Auth.
Sixth: The voting authority, using their hash key, re-hashes the encrypted package, the same as step four above. This should create the exact same hash key, which verifies that the encrypted data was NOT tampered with during transmission to the Voting Authority.
SO [encrypted package] x [Voting Auth Hash Key] should still = [VA Hash Value]
The package can now be stripped of the hash value that was sent with it:
[Encrypted Package]
7th: The Voting Authority takes private key that belongs to them, decrypts the data. Since the package was sent with the VA's public key, the only key that can decrypt it is the private key the VA has. This gets them to here:
[encrypted vote] + [personal id values] + [person's hash key] + [person's hash value] + [person's public key] <-- decrypted with VA's private key.
8th: The voting authority can take the person's hash key, and re-hash the encrypted votes with that person's ID values - if the encrypted vote data and the person's ID data was not tampered with, the hash key should generate the SAME hash value that was sent with all the other data to them.
So ([encrypted vote] + [personal id] + [person's public key]) x [personal hash] should still = [personal hash value]
9th: Since the hash value they generated above should be the same as what was transmitted, the VA can now decrypt the encrypted vote using the person's public key.
The entire process does the following: 1) It makes the vote unalterable. If it is altered, the hash values change and won't match. 2) it makes the vote irrefutable - the person can't say they didn't cast the ballot, because their personal ID is tied to the vote. 3) it makes the the vote nearly 100% unforge-able. Because the vote is tied to the person's personal data that only they will have, it can't be forged and if it is, the person can almost 100% prove they didn't send the vote. 4) no one on either end can tamper with the vote results, and if they do it becomes instantly obvious. 5) LAST, and most important, it makes it so that if there is EVER a question about the vote, an independent party can come in and verify all of the above.
So for those of you who understood every step I described above, what do you think? Leave me some feedback or vote below!
Thanks.
V/R
Marc Wayman
Posted 11 y ago
Responses: 26
yeah, i agree, if an ID card is good enough for our military personnel, it's good enough for the civilians also.
(1)
(0)
I must admit I'm a little confused, but I understand your concept. Once you build a prototype I suggest you try it out in Florida and Wisconsin.
(1)
(0)
SSgt (Join to see)
PO3 Shaun Taylor I was in Florida when the recount was going on and they were interpreting intent. I about lost it. Gore, gore, gore, Common man, there are a lot of elderly R in that area too. If anything this election was nearly stolen and made this country look third world. Win by any means is terrible.
(1)
(0)
Well, if anything, your idea would open up a whole new side industry that would employ quite a few people. The thing with this idea is the fact that there is no such thing as 100% security. There's always going to be some researcher/hacker that will discover some vulnerability in these voting systems. Fraud exists. So does stupidity. You can't get rid of either, whether you're in government, or in industry.
(0)
(0)
Everyone who cares about fair and representative elections, please, please watch this video list.
http://www.cgpgrey.com/politics-in-the-animal-kingdom/
http://www.cgpgrey.com/politics-in-the-animal-kingdom/

Politics in the Animal Kingdom
Homepage for CGP Grey. Videos, articles and links.
(0)
(0)
SFC (Join to see)
Capt Richard I P.: Excellent video (I've watched the first one. Will watch the rest later). Thanks for sharing this!
(1)
(0)
Capt Richard I P.
SFC (Join to see) I'm a huge CGP Grey fan. He makes complex things so understand-able!
(1)
(0)
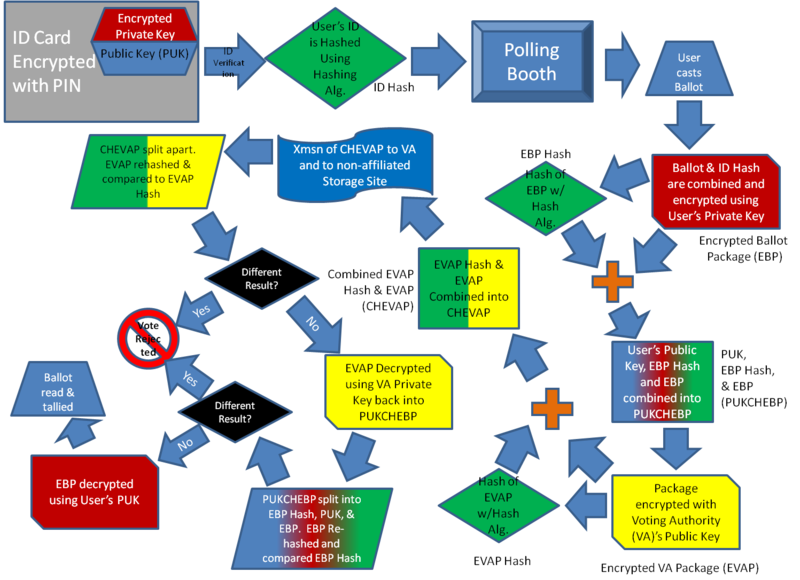
So, for those of you who respond visually better than via verbal: I created a chart that shows the process as I am envisioning it. Yes, it's complicated as hell... but I was running out of room... so youse get's whats youse get's!
(0)
(0)
Ok, here's the short version: encrypt vote, generate a hash so you can verify the data when it's received, encrypt all of that using voting authority's public encryption key, send them the data, they can then decrypt, verify, and tally the vote. The entire process is nearly infallible because it's double encrypted, and each encryption is then hashed, which provides and guarantees data integrity. Since voter's ID is also mixed in to the hash, the voter's ID is also protected from falsification, and doubly serves to prove how the voter voted.
(0)
(0)
SFC (Join to see)
And NOW we have the truth. You are a liberal, who thinks that Democrats have the answers to all of our problems.
And I voted you down not because of your post in general, but because it provided absolutely NO constructive ideas or values, and only spit out liberal talking points.
Take care.
And I voted you down not because of your post in general, but because it provided absolutely NO constructive ideas or values, and only spit out liberal talking points.
Take care.
(0)
(0)
SFC (Join to see)
MSgt Bill Jones : Since you are now resorting to insults, I'm not even going to dignify your idiotic statement with a "proper" response. Please don't respond to my questions, posts, or comments anymore.
(0)
(0)
SFC (Join to see)
Wait... you're upset because I gave you the label "liberal", that you took to be insulting, and you started it off first by saying "Most of the lunatics on this forum" and 2nd calling me "Mr. Orwell" before I ever posted anything about you being a liberal? On top of that, in the latter text of that message, you then disparage all Conservatives and the "wealthy darlings" of the GOP in just ONE sentence as "threat"...
And yet, I insulted you first???? That's almost typical of most liberal mindsets in the first place.. throw out a bunch of insults, then, when the other party throws out a barb or two, blame them for insulting you!
Besides, if you are a liberal, why would you find it insulting for me to call you one? Of course, if you truly are not a liberal or find it insulting to be called that, this make it more likely that you're really just trolling to insult anyone with a radical idea that might actually work or who was looking for honest, well thought opinions (regardless of which side they came from).
And yet, I insulted you first???? That's almost typical of most liberal mindsets in the first place.. throw out a bunch of insults, then, when the other party throws out a barb or two, blame them for insulting you!
Besides, if you are a liberal, why would you find it insulting for me to call you one? Of course, if you truly are not a liberal or find it insulting to be called that, this make it more likely that you're really just trolling to insult anyone with a radical idea that might actually work or who was looking for honest, well thought opinions (regardless of which side they came from).
(0)
(0)
SSG (Join to see)
"..Conservative and wealthy darlings of the GOP.."
7 out of the top 10 wealthiest people in Congress are Democrats... j/s...
7 out of the top 10 wealthiest people in Congress are Democrats... j/s...
(1)
(0)
Read This Next



 Ideas
Ideas Voting
Voting