Posted on Aug 12, 2015
Firewall for Network Security. . . Do you use it? Host or Network?
17K
60
58
4
4
0
Posted 10 y ago
Responses: 15
There are several regulations, edicts, or industry practices that require firewalls between certain types of servers. For the client I develop for at the company I work, there are firewalls between front end, middle wear and database servers. Not to mention there are firewalls separating each client and on the core switch coming into our data-center. For PCI compliance we don't even store credit card information. We've outsourced it to a company that specializes in processing and storing credit card data.
(5)
(0)
GySgt Carl Rumbolo
For business use I tend to favor Checkpoint, at one time I had a Watchguard SOHO device, it was adequate but really didn't meet some of my needs in terms of multiple VPN end points etc - it became an issue around licensing costs. Cisco makes good product, again, licensing can be a cost driver for Cisco (as well as Checkpoint).
I do some level of consulting work on the side for small businesses and for that my go to solution is the Ubiquiti series devices - it's relatively inexpensive, and properly configured very secure - though you really need to know what you are doing. It will meet PCI testing standards, and in addition is fully in line with requirements to meet HIPPA security needs.
I do some level of consulting work on the side for small businesses and for that my go to solution is the Ubiquiti series devices - it's relatively inexpensive, and properly configured very secure - though you really need to know what you are doing. It will meet PCI testing standards, and in addition is fully in line with requirements to meet HIPPA security needs.
(0)
(0)
GySgt Carl Rumbolo
SGT (Join to see) - SSH is not a firewall, so not sure of the relevance. SSH is essentially secure telnet. An access solution.
(0)
(0)
LCpl Arrick Moore
I've used the 4.... Checkpoint, SonicWALL, WatchGuard and Cisco.... I very much prefer the checkpoint, but in order of user configurability and cost of configuration, it would be cheapest to most expensive... watchguard, sonicwall cisco, checkpoint...
(1)
(0)
SGT (Join to see)
LCpl Arrick Moore - Never heard of Checkpoint. You seem to have nothing but great things to say about it, though.
(0)
(0)
(0)
(0)
SGT (Join to see)
SSgt Alex Robinson - Are those suggestions different now? Regardless, can you specify some products to consider?
(0)
(0)
NMCI told me that my network settings are "too paranoid" to work with their laptops. F*** 'em if they can't take a joke!
(2)
(0)
GySgt Carl Rumbolo
Now that is an 'professional' response from an IT person. Seriously, too much security is just as bad as 'too little'. Security controls, including network access controls should be configured to meet the requirements of security while not limiting business processes and functions.
Once you start 'locking' things down for the sake of locking them down, you will quickly find yourself playing whack-a-mole with vulnerabilities as end-users try to work around things. Worse - in a business oriented environment you will quickly alienate your internal customers and find yourself irrelevant and outsourced.
Once you start 'locking' things down for the sake of locking them down, you will quickly find yourself playing whack-a-mole with vulnerabilities as end-users try to work around things. Worse - in a business oriented environment you will quickly alienate your internal customers and find yourself irrelevant and outsourced.
(0)
(0)
Sgt Ken Prescott
I understand, but my network is there to meet my needs, and NMCI was willing to accept risks that I found to be unacceptable. (About a year later, they wound up incorporating my settings because they had been hacked--said hack had been active at the time I had told NMCI that they were taking unacceptable risks for the security of my network. If I had said OK, my family's information would have been compromised.)
(0)
(0)
SGT (Join to see)
Sgt Ken Prescott - They didn't like your higher standard until it proved effective and necessary.
(1)
(0)
Here is the bigger question.....is your firewall configured for "deny-all except for"?
(1)
(0)
PO1 Sojourner "Chancy" Phillips
Agreed. I asked that because I have found that many think that is the absolute for configuring for compliance. They think as long as that is done they are safe. Especially now with the hacker paranoia (rightly so). But the biggest problem I have seen is that "except for" list is not managed as well as it should be especially with pre-production systems being tested into production.
(1)
(0)
We use sonci wall products that have served us very well, the only draw back Dell(hell) now owns them.
(1)
(0)
SGT (Join to see)
You're the second to mention Sonic Wall. Why does no one like Dell? Their customer service was great when I repaired their computers while active.
(0)
(0)
SSG John Erny
SGT (Join to see) - If you can afford their Gold service agreement then they do a pretty good job, for the corporate world who buys their low end products and bottom rate service then they are horrible.
Prior to the GX 260 a really liked Dell, then they were among the first to rush to China and the quality control went to hell, they had a bad run of machines that were a nightmare to trouble shoot. They would have bad mother boards that would fail after running for a few hours, then work again for a while after a reboot plus other hardware issues. Their diagnostics would not catch the issues until you had the machine running on the bench for a few hours.
We switched to HP Business Desktops and Laptops and have had great luck. HP has now killed off their main business model to keep in the same price point as Dell who cuts corners where ever they can so we are switching to the HP Z series work stations which are rock solid!
For my own use I buy parts from new egg and build:
2 x SAPPHIRE Radeon HD 7770 GHz Edition OC 1GB 128-bit GDDR5
1 x CORSAIR Professional Series Gold AX750 (CMPSU-750AX) 750W
1 x Corsair Graphite Series 600T Arctic White Steel / Plastic ATX Mid Tower Computer Case
1 x Corsair Force Series GT CSSD-F180GBGT-BK 2.5" 180GB SATA III Internal Solid State Drive (SSD)
1 x ASUS Black Blu-ray Drive SATA Model BC-12B1ST/BLK/B/AS - OEM
1 x AMD FX-8150 Zambezi 3.6GHz Socket AM3+ 125W Eight-Core Desktop Processor FD8150FRGUBOX
1 x ASUS Sabertooth 990FX AM3+ AMD 990FX SATA 6Gb/s USB 3.0 ATX AMD Motherboard with UEFI BIOS
1 x CORSAIR Vengeance 16GB (4 x 4GB) 240-Pin DDR3 SDRAM DDR3 1600 (PC3 12800) Desktop Memory Model CMZ16GX3M4A1600C9B
OS, what ever I feel like
Prior to the GX 260 a really liked Dell, then they were among the first to rush to China and the quality control went to hell, they had a bad run of machines that were a nightmare to trouble shoot. They would have bad mother boards that would fail after running for a few hours, then work again for a while after a reboot plus other hardware issues. Their diagnostics would not catch the issues until you had the machine running on the bench for a few hours.
We switched to HP Business Desktops and Laptops and have had great luck. HP has now killed off their main business model to keep in the same price point as Dell who cuts corners where ever they can so we are switching to the HP Z series work stations which are rock solid!
For my own use I buy parts from new egg and build:
2 x SAPPHIRE Radeon HD 7770 GHz Edition OC 1GB 128-bit GDDR5
1 x CORSAIR Professional Series Gold AX750 (CMPSU-750AX) 750W
1 x Corsair Graphite Series 600T Arctic White Steel / Plastic ATX Mid Tower Computer Case
1 x Corsair Force Series GT CSSD-F180GBGT-BK 2.5" 180GB SATA III Internal Solid State Drive (SSD)
1 x ASUS Black Blu-ray Drive SATA Model BC-12B1ST/BLK/B/AS - OEM
1 x AMD FX-8150 Zambezi 3.6GHz Socket AM3+ 125W Eight-Core Desktop Processor FD8150FRGUBOX
1 x ASUS Sabertooth 990FX AM3+ AMD 990FX SATA 6Gb/s USB 3.0 ATX AMD Motherboard with UEFI BIOS
1 x CORSAIR Vengeance 16GB (4 x 4GB) 240-Pin DDR3 SDRAM DDR3 1600 (PC3 12800) Desktop Memory Model CMZ16GX3M4A1600C9B
OS, what ever I feel like
(1)
(0)
Having at least one, centrally located firewall, is a sound practice. A common architecture would be your entry point, then your IDS, your firewall, then your DMZ cluster, etc.
We all know that no one system, device, or technique is going to safeguard your system. A Defense in Depth approach (layered security) is the most sound and practical approach to safeguarding IT systems.
We all know that no one system, device, or technique is going to safeguard your system. A Defense in Depth approach (layered security) is the most sound and practical approach to safeguarding IT systems.
(1)
(0)
SSG (Join to see)
We get great training and I'm very grateful for it. I'm happy to share knowledge and advice. It's why we're here!
(1)
(0)
GySgt Carl Rumbolo
That is a relatively simple and straight forward approach, suitable for SOHO and small business environments. Larger and more complex networks may require a different configuration. For example an Extranet channel for 'they-own' devices where an external business partner places equipment in your data center. Load balancing and deep packet inspection, intrusion detection, etc may require additional layers and/or network configurations.
In larger companies, separation of responsibilities is common, for example network engineers do not write firewall policies, firewall engineers don't configure networks. It provides another layer of protection - I can't tell you how many times a network engineer had problems with routing or traffic flow, and 'fixed' it by punching another hole in a firewall, etc.
In larger companies, separation of responsibilities is common, for example network engineers do not write firewall policies, firewall engineers don't configure networks. It provides another layer of protection - I can't tell you how many times a network engineer had problems with routing or traffic flow, and 'fixed' it by punching another hole in a firewall, etc.
(0)
(0)
SSG (Join to see)
Absolutely. In most situations the network engineers are performing the security portion as well. And we all know, in a business setting, that network engineer is going to prioritize through-put instead of balancing it with security.
As a general practice my configuration will work for simple setups. Obviously when you start venturing into Fortune 500 setups, they will have complex setups with many layers of security (if they're doing it right). But I have seen examples of security that are a joke. One example comes to mind of a company separating everything into VLANS behind a single firewall and calling it good. I shake my head when I see stuff like that.
As a general practice my configuration will work for simple setups. Obviously when you start venturing into Fortune 500 setups, they will have complex setups with many layers of security (if they're doing it right). But I have seen examples of security that are a joke. One example comes to mind of a company separating everything into VLANS behind a single firewall and calling it good. I shake my head when I see stuff like that.
(0)
(0)
SGT (Join to see)
Me too. I asked some questions to my router's tech support that their only answer was "this model can't do that" and ufw/gufw still makes my brain melt.
(1)
(0)
GySgt Carl Rumbolo
A product that I would recommend as firewall / router is the Ubiquiti series router/firewall. Either the Edgerouter Pro-8 or the Edgerouter ERPOE-5. I currently have an Pro-8 in my rack at home, and placed ERPOE-5's at my son's home, my in-laws and my folks homes - running VPN tunnels to all three.
The Edgerouter series are relatively inexpensive - approx $400 for the Pro-8, $175 or so for the ERPOE-5), fully featured router and firewall platforms. Fully capable of routing (support for BGP, OSPF,etc) with a true firewall capable of supporting deep packet inspection with complex rule sets, and as mentioned support for VPN - both peering and client configurations.
The code is based on a fork of Vyatta code, it has both a GUI and command line interface that is fairly easy to pickup. Excellent tech support - both from product specialists as well as a deep forum.
The other nice thing about the Pro-8/ERPOE-5 is that they support WAN fail-over. I currently have a Time Warner cable modem and a Windstream DSL connection. The primary is the TW link, with traffic fail over to the DSL in the event of an outage. I have also configured it so the sub-net used for my quest wireless access is routed through the DSL, logically isolating from the rest of the internal network, as well as applying QOS rules to throttle and log guest traffic.
The Edgerouter series are relatively inexpensive - approx $400 for the Pro-8, $175 or so for the ERPOE-5), fully featured router and firewall platforms. Fully capable of routing (support for BGP, OSPF,etc) with a true firewall capable of supporting deep packet inspection with complex rule sets, and as mentioned support for VPN - both peering and client configurations.
The code is based on a fork of Vyatta code, it has both a GUI and command line interface that is fairly easy to pickup. Excellent tech support - both from product specialists as well as a deep forum.
The other nice thing about the Pro-8/ERPOE-5 is that they support WAN fail-over. I currently have a Time Warner cable modem and a Windstream DSL connection. The primary is the TW link, with traffic fail over to the DSL in the event of an outage. I have also configured it so the sub-net used for my quest wireless access is routed through the DSL, logically isolating from the rest of the internal network, as well as applying QOS rules to throttle and log guest traffic.
(2)
(0)
It has been a while since i visited this thread - reading over the responses there are a variety of solutions and ideas. However it is important to remember that firewalls are only one portion of a secure network design.
Firewalls can provide protection against some forms of unauthorized access to network and computing resources but they are in no way a complete security solution.
There are numerous attack vectors that need to be considered, some of which can be mitigated by IDS and/or IPS, others require application level protections and there are also malware detection and removal - including inbound and outbound email scanning.
Single point firewall solutions offer limited defenses, however most well configured (and regularly patched) SOHO 'routers' will provide the basic protections for a typical home environment. Note however none of the typical consumer (and few 'prosumer') routers provide much, if any protection against DOS attacks. Simple DOS attack will often crash a SOHO router and if that router is also the wireless access point (as many are) the entire network crashes.
Professionally, I do not recommend, nor would allow to be deployed any solution that is based on a single point firewall - it should be a layered DMZ configuration. Similarly wireless access points should be separate from a firewall-router.
It should be noted that typical SOHO router-wireless access point devices do not have either the memory or processing power to handle routing, DHCP, DNS relay, wireless management and security. Particularly once you get above more than 10 or 15 client devices. Even leaving out the design needs to ensure quality signal, a single central wireless access point is not a good design.
DNS and DHCP are also things that should be considered. A good secure DHCP plan should set aside a relatively small pool for unregistered devices, and a larger 'reserved' pool for known clients - the known clients are given DHCP reserved addresses. Certain devices should have fixed static address - network devices for example, printers, etc. If possible I recommend 802.1x authentication for clients connecting to switch ports (unmanaged switches are not particularly recommended here).
I generally do not recommend using the ISP provided DNS - a public DNS like Google (8.8.8.8 / 8.8.4.4) is a better choice - you can easily set your DHCP to provide those. Similarly, if you are running any sort of home VPN, getting a DynDNS service (or similar product) and using your OWN registered domain is a good best practice.
Regards!
Firewalls can provide protection against some forms of unauthorized access to network and computing resources but they are in no way a complete security solution.
There are numerous attack vectors that need to be considered, some of which can be mitigated by IDS and/or IPS, others require application level protections and there are also malware detection and removal - including inbound and outbound email scanning.
Single point firewall solutions offer limited defenses, however most well configured (and regularly patched) SOHO 'routers' will provide the basic protections for a typical home environment. Note however none of the typical consumer (and few 'prosumer') routers provide much, if any protection against DOS attacks. Simple DOS attack will often crash a SOHO router and if that router is also the wireless access point (as many are) the entire network crashes.
Professionally, I do not recommend, nor would allow to be deployed any solution that is based on a single point firewall - it should be a layered DMZ configuration. Similarly wireless access points should be separate from a firewall-router.
It should be noted that typical SOHO router-wireless access point devices do not have either the memory or processing power to handle routing, DHCP, DNS relay, wireless management and security. Particularly once you get above more than 10 or 15 client devices. Even leaving out the design needs to ensure quality signal, a single central wireless access point is not a good design.
DNS and DHCP are also things that should be considered. A good secure DHCP plan should set aside a relatively small pool for unregistered devices, and a larger 'reserved' pool for known clients - the known clients are given DHCP reserved addresses. Certain devices should have fixed static address - network devices for example, printers, etc. If possible I recommend 802.1x authentication for clients connecting to switch ports (unmanaged switches are not particularly recommended here).
I generally do not recommend using the ISP provided DNS - a public DNS like Google (8.8.8.8 / 8.8.4.4) is a better choice - you can easily set your DHCP to provide those. Similarly, if you are running any sort of home VPN, getting a DynDNS service (or similar product) and using your OWN registered domain is a good best practice.
Regards!
(0)
(0)
For my personal home network I use a Ubiquiti EdgeRouter Pro as a border gateway. Most of my internal network is Ubiquiti product. I have 2 (soon to be 3) EdgeRouter POE in homes of family for point to point vpn, giving them access to a NAS with 11 TB of family archives (photos, documents, some video)
(0)
(0)
GySgt Carl Rumbolo
I strongly recommend the Ubiquiti product line, it's enterprise grade gear, used by a number of universities, businesses. Their wireless products are outstanding. I have three ceiling mounted access points, Ubiquiti edge switch (24 port POE) and the EdgeRouter PRO. I also have a Cisco SG300-10 as the server / NAS switch.
I have the Ubiquiti and Cisco switches connected via optical fiber (OM4). The internet uplinks are a Time Warner cable modem (350mb down / 100mb up) and a Windstream DSL (10 mb down 5 mb up) - it is in a hot fail over configuration,meaning if I lose the TW connection traffic routes to the DSL side.
Granted it's probably overkill for 98% of the home community, I actually have a closet converted to an IDF, but I also work at home full time.
I have the Ubiquiti and Cisco switches connected via optical fiber (OM4). The internet uplinks are a Time Warner cable modem (350mb down / 100mb up) and a Windstream DSL (10 mb down 5 mb up) - it is in a hot fail over configuration,meaning if I lose the TW connection traffic routes to the DSL side.
Granted it's probably overkill for 98% of the home community, I actually have a closet converted to an IDF, but I also work at home full time.
(1)
(0)
SGT (Join to see)
GySgt Carl Rumbolo - It's been a while. I hope all is well. Have your thoughts on Ubiquiti EdgeRouter series changed with the newer models?
(0)
(0)
GySgt Carl Rumbolo
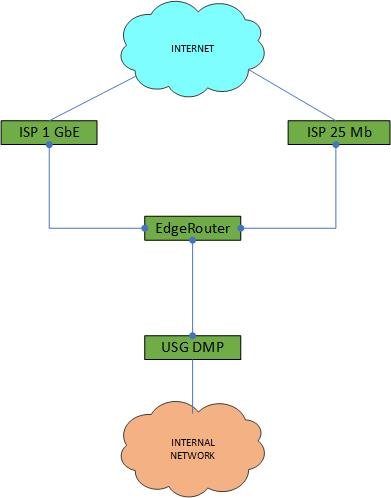
I am currently using an EdgeRouter as an external border gateway / firewall which does failover between two ISP (primary 1 GbE and a secondary backup 25 MB ). If the primary fails, the secondary picks up, once primary comes back, the routing flips. Note that any SSL or VPN links will typically fail when the routes change as the source address changes (the source address the remote side sees is the ISP address assigned to the WAN ports on the Edge Router, The external border also provides both client and point-to-point VPN services.
The internal border is a Ubiquiti Dream Machine Pro with full IDS/IPS and some custom JSON configs. Yes - someone will point out that this is 'dual NAT' - so? Typically internet traffic sees multiple NAT hops through the path. Properly done it's transparent. I do have some limited policy based routing in place the drives some traffic to the lower speed secondary - for example updates and traffic for IP based lights - they are all on a dedicated VLAN (along with most other smart devices to isolate them from user networks.
QOS is enabled for certain traffic - my VPN connectivity for work and streaming for the primary smart TV.
The internal network has 5 Ubiquiti switches (24 -250 and 8-150 models) and 8 APs (a mix of Pro, HD Nano, Mesh and IW). Plus a 10 GbE managed Netgear switch for the NAS environment (48 TB of NAS).
I am covering a 2800 sq foot home, plus outside - coverage is around -45 dB with seamless roaming. Four VLANS - management, device, user and guest - the Ubiquiti guest portal capabilities are pretty nice. It's a total smart home configuration so the robust network is needed - 120 smart IP lights, 16 IP cameras - smart appliances, etc.
At the end of the day, yes it's a fairly complex network for a home environment and overkill for most people - but with a highly integrated smart home and the fact I work from home - it's worth the investment.
The internal border is a Ubiquiti Dream Machine Pro with full IDS/IPS and some custom JSON configs. Yes - someone will point out that this is 'dual NAT' - so? Typically internet traffic sees multiple NAT hops through the path. Properly done it's transparent. I do have some limited policy based routing in place the drives some traffic to the lower speed secondary - for example updates and traffic for IP based lights - they are all on a dedicated VLAN (along with most other smart devices to isolate them from user networks.
QOS is enabled for certain traffic - my VPN connectivity for work and streaming for the primary smart TV.
The internal network has 5 Ubiquiti switches (24 -250 and 8-150 models) and 8 APs (a mix of Pro, HD Nano, Mesh and IW). Plus a 10 GbE managed Netgear switch for the NAS environment (48 TB of NAS).
I am covering a 2800 sq foot home, plus outside - coverage is around -45 dB with seamless roaming. Four VLANS - management, device, user and guest - the Ubiquiti guest portal capabilities are pretty nice. It's a total smart home configuration so the robust network is needed - 120 smart IP lights, 16 IP cameras - smart appliances, etc.
At the end of the day, yes it's a fairly complex network for a home environment and overkill for most people - but with a highly integrated smart home and the fact I work from home - it's worth the investment.
(0)
(0)
The real question is not if someone uses a firewall - the question is what version and how is it configured. A SOHO firewall router with known unpatched vulnerabilities or one that is poorly configured is just bad if not worse than no firewall at all (probably worse since the the user has a false sense of security)
Also firewalls are not the be all,end all of security. Solid best practices, good passwords frequently changed, as well as intrusion detection and deep packet inspection are all parts of a good security implementation.
Some things to think about (there are alot more)
Are you enforcing end-point security for desktop clients with robust authentication schemes?
Do you practice AAA - Authentication, Authorization and Accounting?
Are you using role based security - locking down administrative privilege and access?
Secure backups of data ?
End user training around best practices?
Application security - do you know what the traffic flow pattern is for all your applications?
Audit policies , penetration testing?
Also firewalls are not the be all,end all of security. Solid best practices, good passwords frequently changed, as well as intrusion detection and deep packet inspection are all parts of a good security implementation.
Some things to think about (there are alot more)
Are you enforcing end-point security for desktop clients with robust authentication schemes?
Do you practice AAA - Authentication, Authorization and Accounting?
Are you using role based security - locking down administrative privilege and access?
Secure backups of data ?
End user training around best practices?
Application security - do you know what the traffic flow pattern is for all your applications?
Audit policies , penetration testing?
(0)
(0)
Read This Next


 Information Technology
Information Technology Computers
Computers Network Security
Network Security Information Assurance
Information Assurance